Security
Every download or upload activity is recorded and stored in a log file. Every line in every document is counted automatically to eliminate any billing errors. All systems are backed up on a daily basis. Our servers are fully protected by security certificates and passwords. We have additional servers for redundancy. We have built simple and effective tools for electronic signatures, faxing, emailing, real time reporting, uploading of audio dictation and downloading of documents.
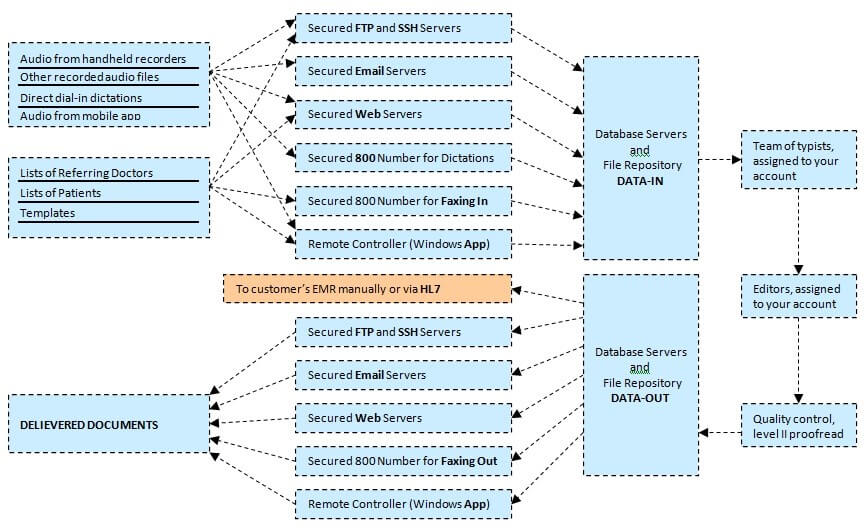
Our customers send us thousands of files (audio, patient lists, lists of referring doctors, templates) daily; each file is protected and safely stored in the repository. Our customers have a choice of file transfers (Secure File Transfer Protocol or secure email, web interfaces or Remote Controller, dial-in or faxing).
Our system is a complex combination of software and hardware. There is a central web server; it has virtually no limits when it comes to the amount of traffic, space and users it can handle. We have email, database, FTP and storage servers linked to our web server 24/7; and there are multiple telephony servers for phone-in dictations. In addition, our database is backed up on a daily basis to two different sites. We will maintain a permanent backup for all your transcription work as long as you are our customer at no charge.
Most of our servers are Linux-based. In addition to having standard protection features such as firewalls, anti-virus and scheduled system upgrades, we enforce several other security measures. For example, our Apache and PHP are always running in the safe mode. In addition to firewalls, our code can also distinguish different types of hacker attacks and defend our systems against them. Our email servers have the same password rules and regulations as web servers